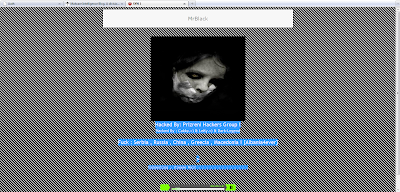
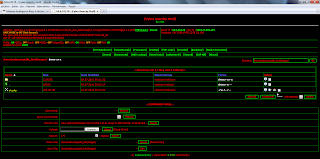
Phishing attacks are increasingly common and are no longer confined as in the beginning to use as cover only banks, and any service offered over the Internet and requires username and password, sooner or later will be grounds target for criminals.
PayPal isn't a new service and was one of the first to offer e-commerce services, whose image is one of the most commonly used for phishing. Starting today, July 4 (Independence Day U.S.) has been active phishing a massive campaign against PayPal.
The Defacing seen in the image is as a seal of the executives in each of the sites involved which holds the fake PayPal page along with the fraudulent file package.
Updated 04.07.2010
New active domains. Unlike the first "litter" of vulnerable sites, in this case the phishing package is housed in the folder
/~radiocon/ and all they implanted a backdoor (PHP Shell) through
uk.php file.
4dalove.org/~radiocon/security-cod/webscr.php
4less.tv/~radiocon/security-cod/webscr.php
64.6.241.8/~radiocon/security-cod/webscr.php
64.6.242.186/~radiocon/security-cod/webscr.php
64.6.242.50/~radiocon/security-cod/webscr.php
64.6.242.60/~radiocon/security-cod/webscr.php
64.6.242.78/~radiocon/security-cod/webscr.php
64.6.243.76/~radiocon/security-cod/webscr.php
888sandngravel.com/~radiocon/security-cod/webscr.php
aa.org/~radiocon/security-cod/webscr.php
aama.com.ar/~radiocon/security-cod/webscr.php
aikiti.ch/~radiocon/security-cod/webscr.php
alasparalamente.com.ar/~radiocon/security-cod/webscr.php
anthonybabyska.com/~radiocon/security-cod/webscr.php
arthaus.us/~radiocon/security-cod/webscr.php
b2bwebcreations.com/~radiocon/security-cod/webscr.php
badboybulls.com/~radiocon/security-cod/webscr.php
behlafamily.com/~radiocon/security-cod/webscr.php
benny.co.za/~radiocon/security-cod/webscr.php
bigmindrecords.com/~radiocon/security-cod/webscr.php
blakelybears.org/~radiocon/security-cod/webscr.php
box2.host1free.com/~barbad/emikrazie/update.php
breathoflifetribe.com/~radiocon/security-cod/webscr.php
buckinbull.com/~radiocon/security-cod/webscr.php
buschdesign.com/~radiocon/security-cod/webscr.php
buy4less.ch/~radiocon/security-cod/webscr.php
cabvideoproductions.com/~radiocon/security-cod/webscr.php
caercdelu.org.ar/~radiocon/security-cod/webscr.php
cairncomm.com/~radiocon/security-cod/webscr.php
calculusproductions.com/~radiocon/security-cod/webscr.php
call-complete.com/~radiocon/security-cod/webscr.php
caminosdelser.com.ar/~radiocon/security-cod/webscr.php
canyonconveying.com/~radiocon/security-cod/webscr.php
casagueroonline.com/~radiocon/security-cod/webscr.php
casatrend.com/~radiocon/security-cod/webscr.php
ccflecuador.com/~radiocon/security-cod/webscr.php
centurysecuritypa.com/~radiocon/security-cod/webscr.php
championship.ch/~radiocon/security-cod/webscr.php
championshipsports.com/~radiocon/security-cod/webscr.php
chhetrylaw.com/~radiocon/security-cod/webscr.php
citizenworld.co.za/~radiocon/security-cod/webscr.php
clubalouette.ca/~radiocon/security-cod/webscr.php
complejo-corralito.com.ar/~radiocon/security-cod/webscr.php
complejolasmoras.com.ar/~radiocon/security-cod/webscr.php
congresodeturismodeentrerios.com/~radiocon/security-cod/webscr.php
corporatecolors.net/~radiocon/security-cod/webscr.php
costantinorocca-golfacademy.com/~radiocon/security-cod/webscr.php
cybertrek.co.za/~radiocon/security-cod/webscr.php
cybertrek.org/~radiocon/security-cod/webscr.php
danielcarbone.com.ar/~radiocon/security-cod/webscr.php
danielhoc.com.ar/~radiocon/security-cod/webscr.php
didjrhythm.com/~radiocon/security-cod/webscr.php
digimael.com/~radiocon/security-cod/webscr.php
donaldgrogers.com/~radiocon/security-cod/webscr.php
dougbusch.com/~radiocon/security-cod/webscr.php
ecuadoralaventa.com/~radiocon/security-cod/webscr.php
elegantmoments.com/~radiocon/security-cod/webscr.php
elpatoviganoni.com.ar/~radiocon/security-cod/webscr.php
emilioflores.com/~radiocon/security-cod/webscr.php
ericlawtonlaw.com/~radiocon/security-cod/webscr.php
ericlawtonphotography.com/~radiocon/security-cod/webscr.php
escueladeparteras.com.ar/~radiocon/security-cod/webscr.php
estimulosadecuados.com.ar/~radiocon/security-cod/webscr.php
everydaygandhis.org/~radiocon/security-cod/webscr.php
exclusiveflowersecuador.com/~radiocon/security-cod/webscr.php
faltlaw.com/~radiocon/security-cod/webscr.php
familyaffair.us/~radiocon/security-cod/webscr.php
fire-xpert.com/~radiocon/security-cod/webscr.php
fotoclub-capriasca.ch/~radiocon/security-cod/webscr.php
fullmoonrisingmusic.com/~radiocon/security-cod/webscr.php
gharekabab.com/~radiocon/security-cod/webscr.php
grupoprovedatos.com/~radiocon/security-cod/webscr.php
hamsterworks.com/~radiocon/security-cod/webscr.php
hartbuilt.com/~radiocon/security-cod/webscr.php
housedatabank.com/~radiocon/security-cod/webscr.php
http://danziskie.com/~radiocon/security-cod/webscr.php
hydro-marine.com/~radiocon/security-cod/webscr.php
hydro-marine.net/~radiocon/security-cod/webscr.php
imageavpro.com/~radiocon/security-cod/webscr.php
immigrationattorney.org/~radiocon/security-cod/webscr.php
ismit.com/~radiocon/security-cod/webscr.php
jalanjalanimports.com/~radiocon/security-cod/webscr.php
jeffandlynette.com/~radiocon/security-cod/webscr.php
jessebarish.com/~radiocon/security-cod/webscr.php
jimmiewalden.com/~radiocon/security-cod/webscr.php
jletecnologiasweb.com/~radiocon/security-cod/webscr.php
jojoalves.com/~radiocon/security-cod/webscr.php
kaminimusic.com/~radiocon/security-cod/webscr.php
khasskhass.com/~radiocon/security-cod/webscr.php
kinggraphics.com/~radiocon/security-cod/webscr.php
lactancia.com.ar/~radiocon/security-cod/webscr.php
latinrootstravel.com/~radiocon/security-cod/webscr.php
lexafina.com/~radiocon/security-cod/webscr.php
liberaldemocracynepal.org/~radiocon/security-cod/webscr.php
libra-indumentaria.com.ar/~radiocon/security-cod/webscr.php
liveforspeed.ch/~radiocon/security-cod/webscr.php
loveastruth.com/~radiocon/security-cod/webscr.php
mailrise.net/~radiocon/security-cod/webscr.php
malcantone.com/~radiocon/security-cod/webscr.php
malibusound.com/~radiocon/security-cod/webscr.php
merrychristmas.ch/~radiocon/security-cod/webscr.php
michaelmolluramusic.com/~radiocon/security-cod/webscr.php
movisocialmisiones.com.ar/~radiocon/security-cod/webscr.php
mpscomex.com.ar/~radiocon/security-cod/webscr.php
mujersabia.com.ar/~radiocon/security-cod/webscr.php
multinacionaltransportadora.com/~radiocon/security-cod/webscr.php
municaseros.gov.ar/~radiocon/security-cod/webscr.php
myaccount.elegantmoments.com/~radiocon/security-cod/webscr.php
nepalcouncil.org/~radiocon/security-cod/webscr.php
nepalembassyusa.org/~radiocon/security-cod/webscr.php
nepaliman.com/~radiocon/security-cod/webscr.php
nepalstudycenter.org/~radiocon/security-cod/webscr.php
nepaltvusa.com/~radiocon/security-cod/webscr.php
network.b2bwebcreations.com/~radiocon/security-cod/webscr.php
novaggio.com/~radiocon/security-cod/webscr.php
nrn.nepalcouncil.org/~radiocon/security-cod/webscr.php
nufaro.com/~radiocon/security-cod/webscr.php
oddandrandom.com/~radiocon/security-cod/webscr.php
okolexproperties.com/~radiocon/security-cod/webscr.php
onelovebeauty.net/~radiocon/security-cod/webscr.php
padreswaldorf.com.ar/~radiocon/security-cod/webscr.php
passiveincomesecrets.com/~radiocon/security-cod/webscr.php
pearlregmifineart.com/~radiocon/security-cod/webscr.php
pelusolandi.com/~radiocon/security-cod/webscr.php
peppesbest.com/~radiocon/security-cod/webscr.php
perraultcorp.com/~radiocon/security-cod/webscr.php
phoolbari.com/~radiocon/security-cod/webscr.php
photo.com/~radiocon/security-cod/webscr.php
pogplace.com/~radiocon/security-cod/webscr.php
premraja.com/~radiocon/security-cod/webscr.php
prewiringlaredo.com/~radiocon/security-cod/webscr.php
produccionesdelsol.com/~radiocon/security-cod/webscr.php
publicidadmontanana.com.ar/~radiocon/security-cod/webscr.php
publinetwork.ch/~radiocon/security-cod/webscr.php
puertopiapsa.com/~radiocon/security-cod/webscr.php
qmbsales.com.au/~radiocon/security-cod/webscr.php
radio9fm.com.ar radio9fm.com.ar/~radiocon/security-cod/webscr.php
radiodovaan.com/~radiocon/security-cod/webscr.php
rajeshshakya.com/~radiocon/security-cod/webscr.php
ranchometals.com/~radiocon/security-cod/webscr.php
redgfu.org.ar/~radiocon/security-cod/webscr.php
ristoranteilcastagneto.com/~radiocon/security-cod/webscr.php
robinbvance.com/~radiocon/security-cod/webscr.php
ronyentertainment.com/~radiocon/security-cod/webscr.php
russiancultureinnepal.org/~radiocon/security-cod/webscr.php
sagarmathatv.us/~radiocon/security-cod/webscr.php
saharapc.com/~radiocon/security-cod/webscr.php
selfdefencesecrets.com/~radiocon/security-cod/webscr.php
sharmilauprety.com/~radiocon/security-cod/webscr.php
shilohouse.org/~radiocon/security-cod/webscr.php
shopmynepa.com/~radiocon/security-cod/webscr.php
showbizconsultants.com/~radiocon/security-cod/webscr.php
silverwingsmultimedia.com/~radiocon/security-cod/webscr.php
simracing.ch/~radiocon/security-cod/webscr.php
siyavuya.com/~radiocon/security-cod/webscr.php
skoz.net/~radiocon/security-cod/webscr.php
slpkorea.com/~radiocon/security-cod/webscr.php
soniacavia.com.ar/~radiocon/security-cod/webscr.php
sonicfarm.com/~radiocon/security-cod/webscr.php
starsonstageinc.com/~radiocon/security-cod/webscr.php
sunboonitiri.com/~radiocon/security-cod/webscr.php
superlarge.com/~radiocon/security-cod/webscr.php
tabmanagement.com/~radiocon/security-cod/webscr.php
teatroelatajo.com.ar/~radiocon/security-cod/webscr.php
thebridgenetwork.org/~radiocon/security-cod/webscr.php
thehimalayanhouse.com/~radiocon/security-cod/webscr.php
thevillageii.com/~radiocon/security-cod/webscr.php
tierrasdelacienaga.com.ar/~radiocon/security-cod/webscr.php
timelessimagesofisrael.com/~radiocon/security-cod/webscr.php
tonicomsa.com/~radiocon/security-cod/webscr.php
topangacollective.com/~radiocon/security-cod/webscr.php
tplenterprises.com/~radiocon/security-cod/webscr.php
trancasturtlerescue.com/~radiocon/security-cod/webscr.php
truewordofgodchurch.org/~radiocon/security-cod/webscr.php
turnkeywebmasters.net/~radiocon/security-cod/webscr.php
ucruruguay.com.ar/~radiocon/security-cod/webscr.php
unseenpictures.com/~radiocon/security-cod/webscr.php
uomo.ch/~radiocon/security-cod/webscr.php
usatoyou.com/~radiocon/security-cod/webscr.php
varietytrucksales.com/~radiocon/security-cod/webscr.php
vergogna.ch/~radiocon/security-cod/webscr.php
virtualcar.ch/~radiocon/security-cod/webscr.php
waterfordav.com/~radiocon/security-cod/webscr.php
webfixnow.com/~radiocon/security-cod/webscr.php
wigbeauty.co.za/~radiocon/security-cod/webscr.php
wigbeauty.com/~radiocon/security-cod/webscr.php
winonline.co.za/~radiocon/security-cod/webscr.php
wowwomenontopoftheworld.com/~radiocon/security-cod/webscr.php
wvpatransport.com/~radiocon/security-cod/webscr.php
xkeep.net/~radiocon/security-cod/webscr.php